Learn how to set up a secure custom domain for Intercom Articles using Azure Front Door (Classic) and Terraform.
Intercom is a Customer Communications Platform. It shows who uses your product or website and makes the communication with customers through targeted content, behavior-driven messages, and conversational support more comprehensible.
When you turn your Articles Help Center on, the content is available through intercom.help by default. Your URL will look like this: intercom.help/exampleapp
If you’d like to use a different URL, you can create one by setting up a custom domain in Intercom Articles UI center. The main challenge is to make HTTPS work properly for a created custom domain since Intercom does not provide automatic generation of SSL certificates on their server-side. One of the solutions is to use a third-party DNS provider, through which you can handle SSL certificates. For that purpose, we use the Azure Front Door (Classic) service, which is Microsoft’s global and scalable entry point that uses Microsoft’s global network to provide dynamic application acceleration, load balancing, and security. One of the key features of this service is the cost-free autorotation of managed SSL certificates. The diagram below shows the overall solution setup and communication flow.

Let’s now take a closer look at the Azure Front Door service itself. When you are planning to create and use the Azure Front Door service, you can see that Microsoft has several offerings to use. You can explore them by clicking on “Explore other offerings” in the portal.
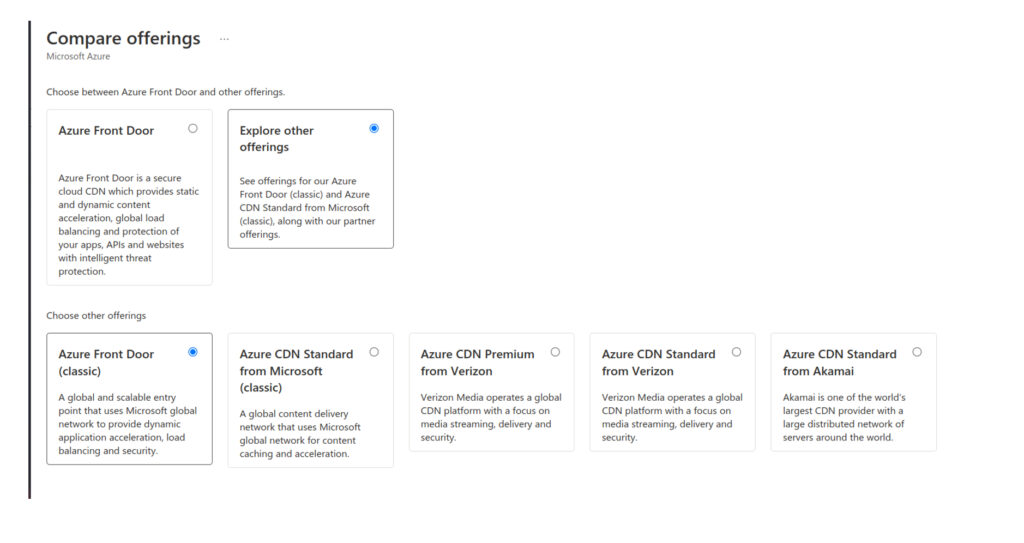
Azure Frontdoor
The first offering called Azure Front Door is a new service version called Azure Front Door Standard and Premium which went into preview in February 2021 and became generally available in March 2022. It has additional enhancements compared to Azure Front Door (classic). The most crucial one is that it combines the capabilities of Azure Front Door (classic), Azure CDN (Content Delivery Network) Standard from Microsoft (classic), and Azure Web Application Firewall (WAF).
Key service features are:
- deliver your dynamic and static content quickly and globally across the globe via Edge locations
- monitoring traffic in real-time
- enhanced metrics and logging analytics
- simple and cost-effective
- advanced rules engine on edge locations supporting regular expressions to create more complex and dynamic routing between users and backends
- built-in layer 3-4 DDoS protection
- attached Web Application Firewall (WAF) and Azure DNS to protect your domainssupport for Azure Private Link
For our solution, we will use just the Azure Front Door (classic) service. Although this service type does not provide features such as capabilities of Azure CND or Azure Private link, we decided to use it in our scenario for several reasons.
- Our simple use case for setting up SSL-based communication with Intercom Articles server does not require the features mentioned above.
- We are managing infrastructure for our customers via Terraform and Azure Front Door (classic) resource is only available. New terraform resources supporting Azure Front Door Standard and Premium tier are still under development.
- Azure Front Door service is still fully supported by Azure.
To make a custom domain work with HTTPS, we need to properly configure Azure Front Door (classic) service and create a CNAME record in your DNS provider to point to that Front Door resource.
Configuration
Azure Front Door (classic) configuration via the portal:
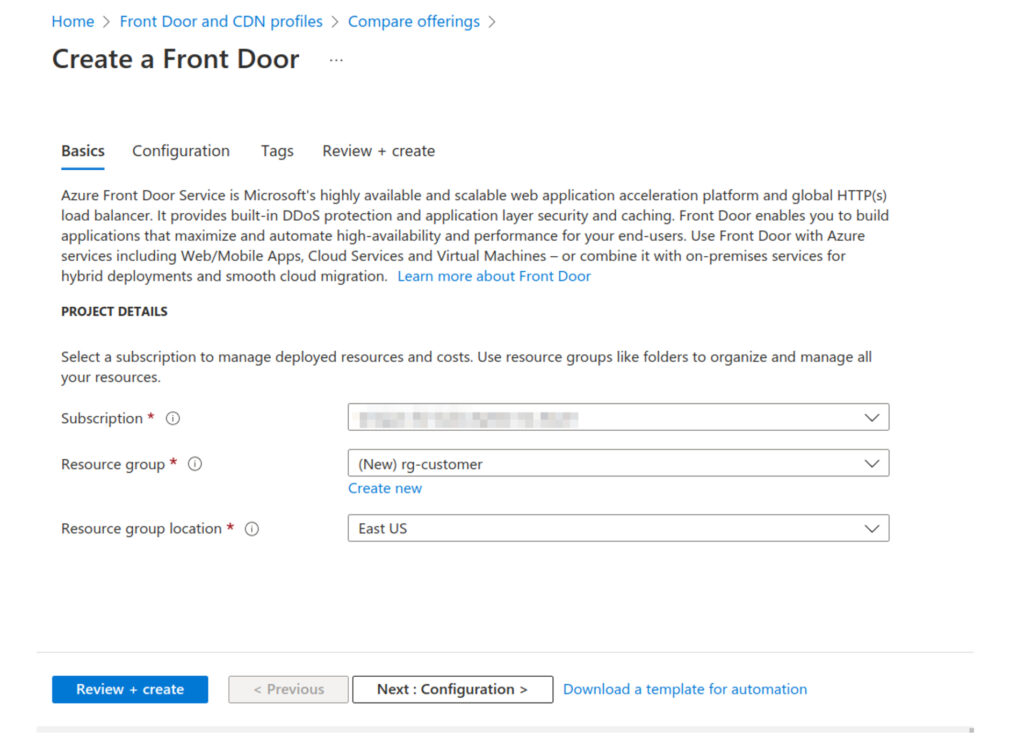
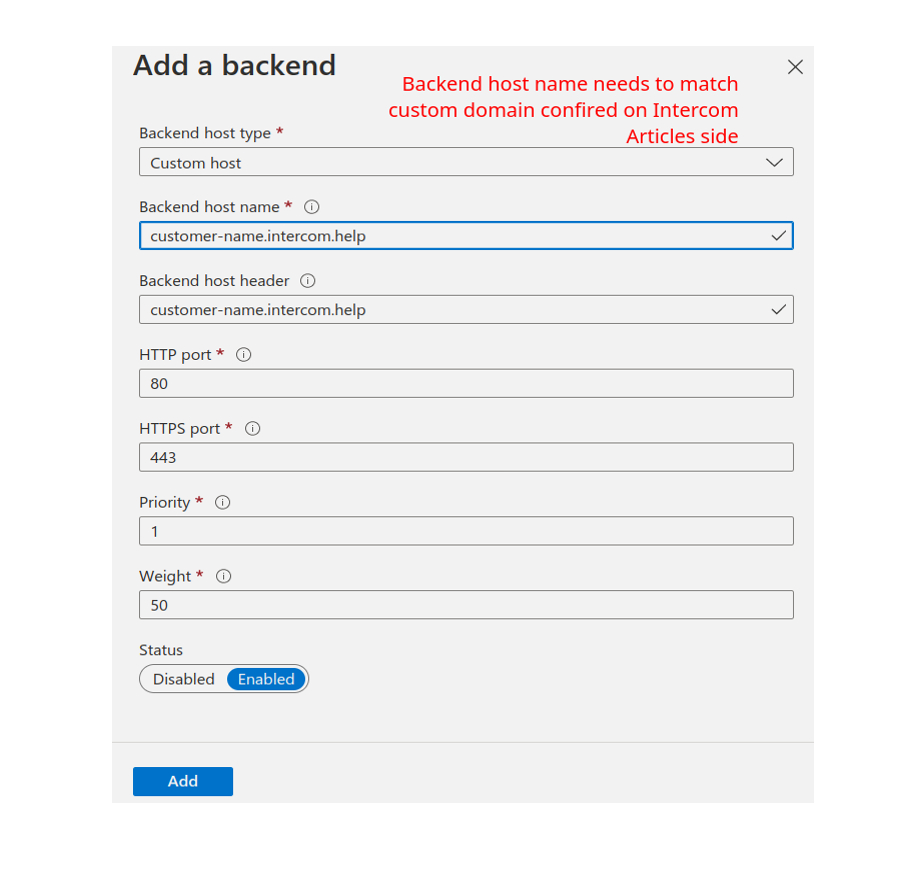
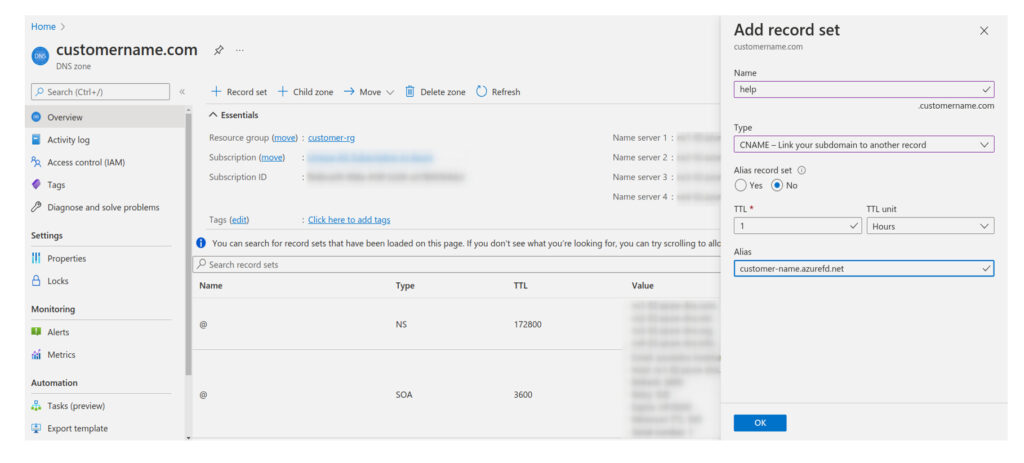
Open your Azure DNS customername.com and add a CNAME record pointing to the Azure Front Door default domain.
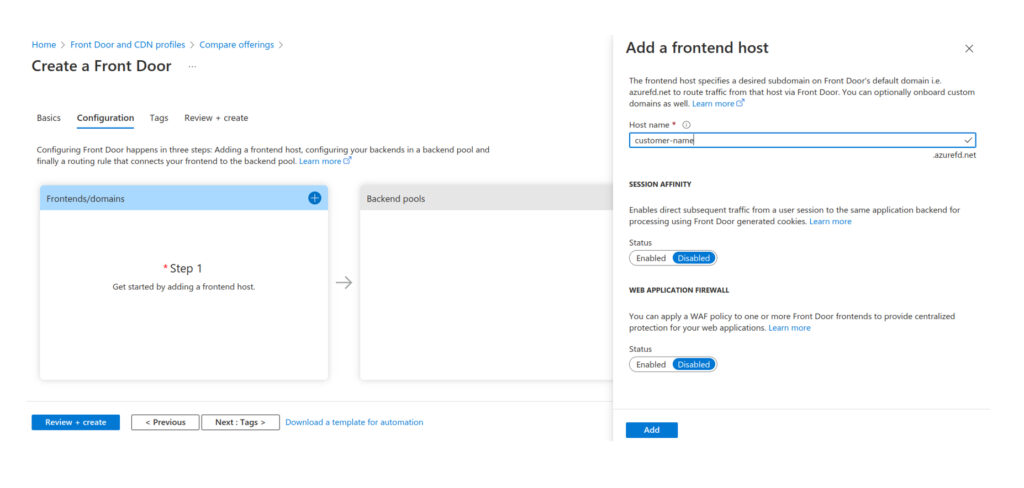
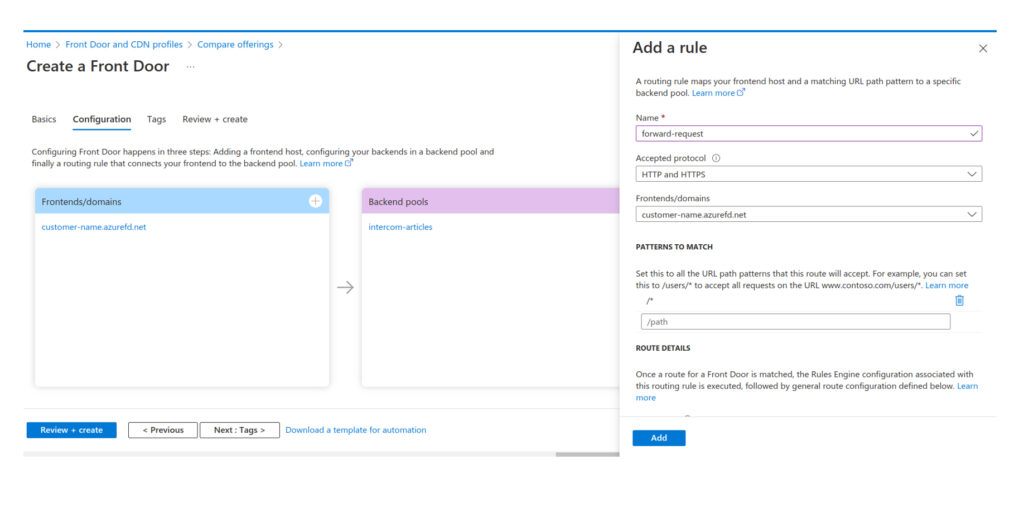
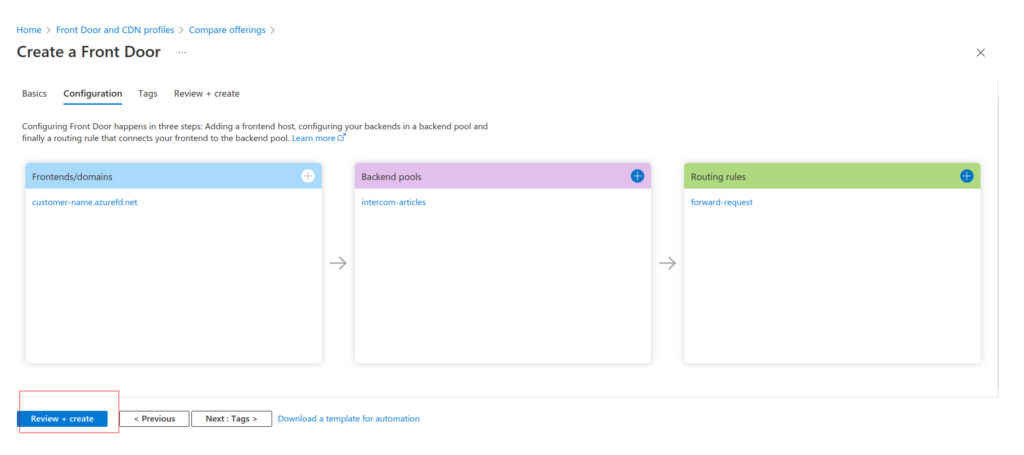
Open created resource, switch to Front Door designer and add a new custom Frontend domain.
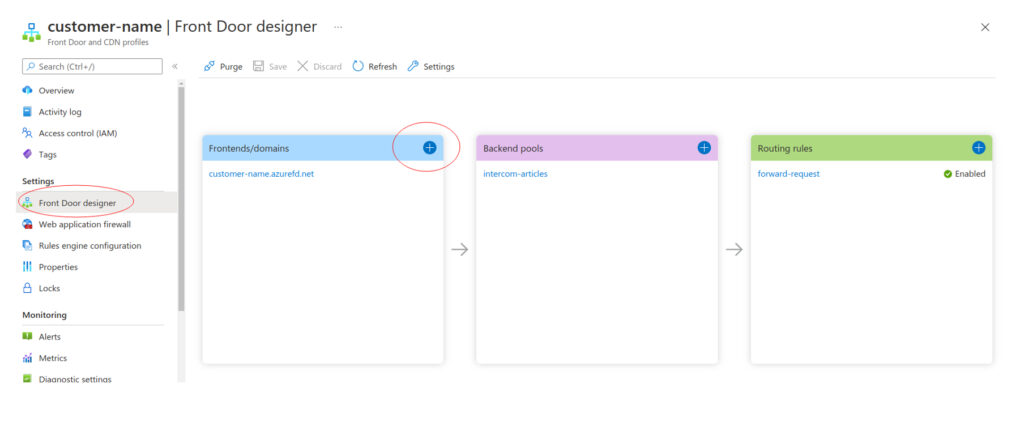
Add frontend custom domain and enable HTTPS.
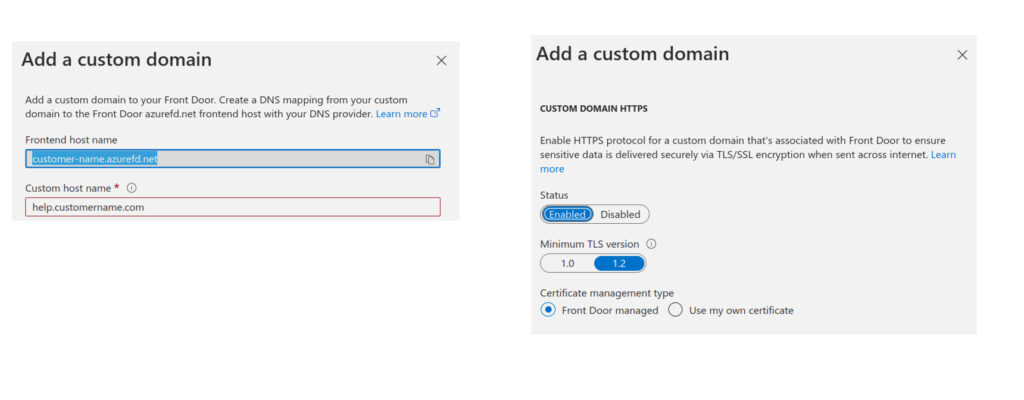
Click Add and wait for Azure Front Door to provision SSL certificates for you.
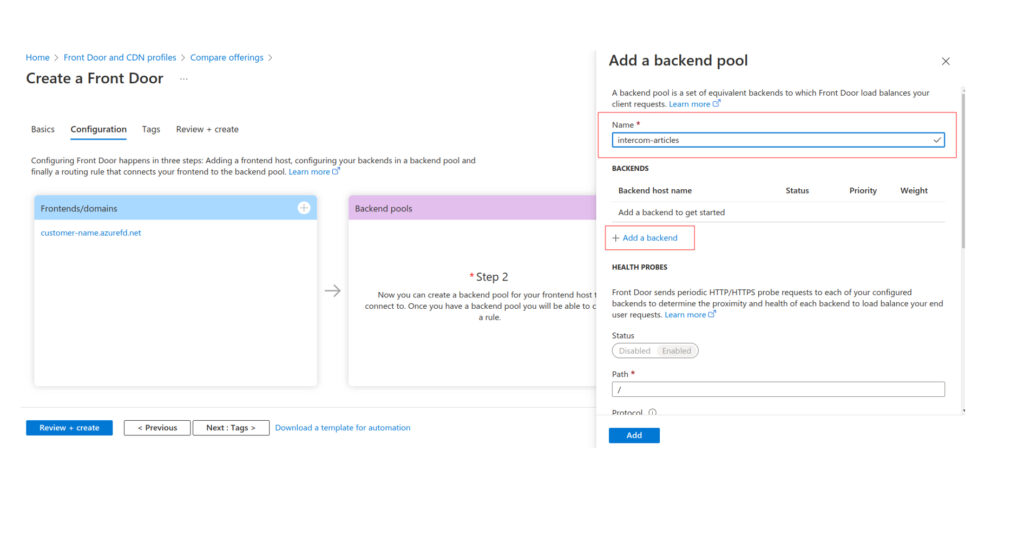
Then edit the routing rule and switch from default Frontends/domains to the new custom domain help.customername.com with SSL enabled. Additionally, you can disable heath probes in the backend pool configuration.
Everything described above can be handled by Terraform code snippet below.
terraform resource:
resource "azurerm_frontdoor" "front_door" {
name = "<front_door_name>"
resource_group_name = <rg_name>
enforce_backend_pools_certificate_name_check = true
backend_pools_send_receive_timeout_seconds = 30
friendly_name = "<customer_name>"
frontend_endpoint {
name = "customer"
host_name = "customer.azurefd.net"
}
frontend_endpoint {
name = "help-customer-app"
host_name = "help.customer.app"
}
backend_pool_load_balancing {
name = "customerFrontDoorLoadBalancingSettings"
}
backend_pool_health_probe {
name = "customerFrontDoorHealthProbeSettings"
enabled = false
interval_in_seconds = 30
probe_method = "HEAD"
protocol = "Https"
}
backend_pool {
name = "intercom-articles"
backend {
host_header = "custom.intercom.help"
address = "custom.intercom.help"
http_port = 80
https_port = 443
}
load_balancing_name = "customerFrontDoorLoadBalancingSettings"
health_probe_name = "customerFrontDoorHealthProbeSettings"
}
routing_rule {
name = "forward-request"
accepted_protocols = ["Http", "Https"]
patterns_to_match = ["/*"]
frontend_endpoints = ["help-customer-app"]
forwarding_configuration {
forwarding_protocol = "MatchRequest"
backend_pool_name = "intercom-articles"
}
}
depends_on = [azurerm_dns_cname_record.intercom_articles]
}
resource "azurerm_frontdoor_custom_https_configuration" "help_customer_app" {
frontend_endpoint_id = azurerm_frontdoor.front_door.frontend_endpoints["help-customer-app"]
custom_https_provisioning_enabled = true
custom_https_configuration {
certificate_source = "FrontDoor"
}
}
Customer DNS configuration:
- Create a CNAME record in Customer DNS to point to the Azure Front Door instance.

terraform resource:
resource "azurerm_dns_cname_record" "intercom_articles" {
name = "help"
zone_name = <zone_name>
resource_group_name = <rg_name>
ttl = 3600
record = "customer.azurefd.net"
}
Conclusion
That’s all. Overall communication with Intercom Articles is now protected over HTTPS using valid SSL certificates leveraging Azure Front Door (classic) service. It is needed to be mentioned that setting up everything via the Azure portal takes time and mistakes may occur easily. On the other hand, Terraform is a very powerful and great declarative language for describing your Infrastructure as code. Therefore, we recommend doing as little manual interventions in your cloud infrastructure as possible.







